Example Of Yara Rule
Allows download of a complete rules file all Yara rules from this repo in one file for convenience from the Actions tab Artifacts see image below. Identifiers must follow the same lexical conventions of the C programming language they can contain any alphanumeric character and the underscore character but the first character can not be a digit.
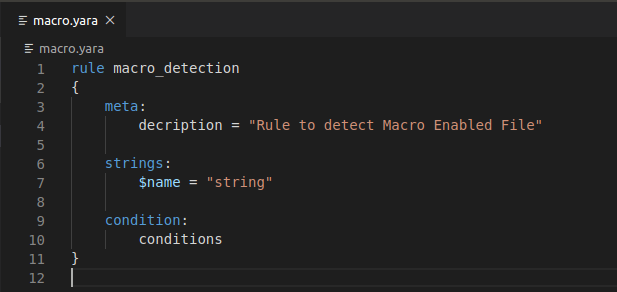
Malware Analysis Introduction To Yara By Ammad Ali Medium
We will use this example as an opportunity to illustrate how the creation of these custom YARA rules was performed.

Example of yara rule. The Yara Rules project aims to be the meeting point for Yara users by gathering together a ruleset as complete as possible thusly providing users a quick way to get Yara ready for usage. Counting is what is sounds like and leverages the count of some element as part of its logic and it can be equal not equal greater than less than etc. In a previous post we created YARA rules to detect compromised CCleaner executables YARA rules to detect compromised CCleaner executables.
Sufficiently Generic Yara Rules. The YARA rule has 3 conditions that must be satisfied. Text_string1 or text_string2 The rule shown above is named vendor and looks for the strings Vendor name and Alias name.
0-9a-fA-F 32 re2 state. A rule is a description based on textual or binary patterns. Yet Another RecursiveRidiculous Acronym YARA is a tool used to identify and classify malware samples.
Text_string1 Vendor name wide text_string2 Alias name wide condition. Here is an example of such an image. We hope this project is useful for the Security Community and all Yara Users and are looking forward to your feedback.
However the real tragedy is that most of the rules are far too specific to match on more than one sample and are therefore almost as useful as a file hash. The file must start with FFD8. YARA works by ingesting rules and applying the logic in the rules to identify malicious files or processes.
For example lets analyze if a random file is a PDF using YARA. However the YARA rule syntax is quite rich consult the Writing YARA Rules guide. 45 78 69 66 00.
YARA identifies and classifies malware based on custom rules created in your PhishER platform. Re1 and re2 This will catch any md5 string it finds in either state. As I said in the introduction rules that generate false positives are pretty annoying.
Minimum Yara version needed. Eval function inside Exif data tested with a regular expression. Enclosed in forward slashes instead of double quotes like Perl Programming yara allows for RegEx.
A rules description can be broken down into three sections. Example 6 Detection Choices. This rule perhaps does not have much magic but it does showcase a few more functions of the YARA-L language today.
Location is using where the element appears in the file as a means of detection. A -bxor 35 condition. Figure 1 YARA Bounding Box example Some other useful techniques are counting location and procession or the order of elements appearing.
Rule RegularShow strings. Rule CaseInsensitiveTextExample strings. WevalsCondition 1 is straightforward.
Each rule in YARA starts with the keyword rule followed by a rule identifier. What I tend to do with the rules is to check all the strings and put. Text_string foobar nocase condition.
If either of those strings is found then the result of the rule is true. An example of this would be a rule that detects the specific xor key used in a type of PowerShell 14 stager that is known to deliver shellcode or Cobalt Strike reflective loaders. JPEG magic header FFD8 tested with.
V330 is minimally needed as some rules may require a specific module. The RULES_FILE points to a file that stores the YARA rules that you want to use while TARGET points to a file a folder or a process to be scanned. To run YARA from the command line run the command.
The above rule is telling YARA that any file containing one of the three strings must be reported as silent_banker. Nessus supports all of the YARA 34 built-in keywords. A This rule targets a category of file used during the delivery stage of intrusion.
Yara OPTIONS RULES_FILE TARGET. For the purpose of this blog we will write a couple of very simple rules. This is just a simple example more complex and powerful rules can be created by using wild-cards case-insensitive strings regular expressions special operators and many other features that youll find explained in YARAs documentation.
Text strings in YARA are case-sensitive by default however you can turn your string into case-insensitive mode by appending the modifier nocase at the end of the string definition in the same line. Rule identifiers are case sensitive and cannot exceed 128 characters. In its blog post Talos shared 3 hashes as Indicators Of Compromise IOCs.
Lets look at an easy example.

Explained Yara Rules Malwarebytes Labs Malwarebytes Labs
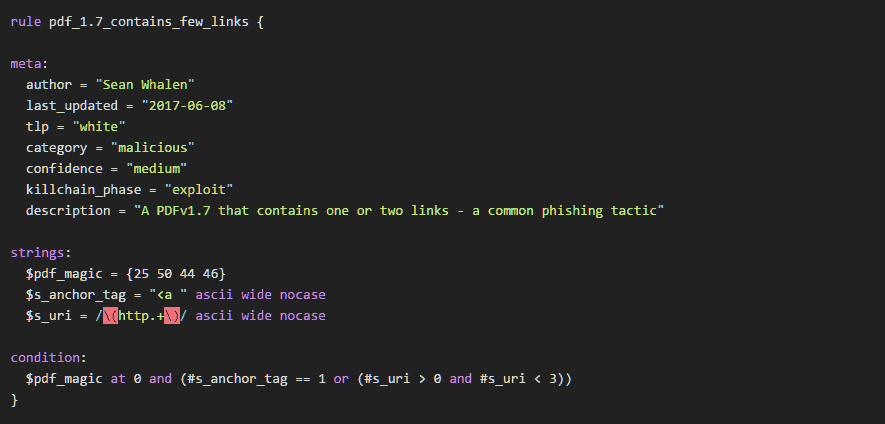
How To Install Yara And Write Basic Yara Rules To Identify Malware Seanthegeek Net
Yara Rules Ntlm Credentials Theft Via Pdf Files Rule At Master Inquest Yara Rules Github
R2yara Use Cases Md At Master Yara Rules R2yara Github

Pin By Yara Aguilera On English Words English Learning Spoken English Vocabulary Words Learn English Words

Yara Rule Examples Knowledge Base

Yara Rule Examples Knowledge Base
Yara Rules Example Yara At Master Godaddy Yara Rules Github
Schema Of The Process Of Generation Of A Yara Rule In The First Phase Download Scientific Diagram

Yara Rule Examples Knowledge Base
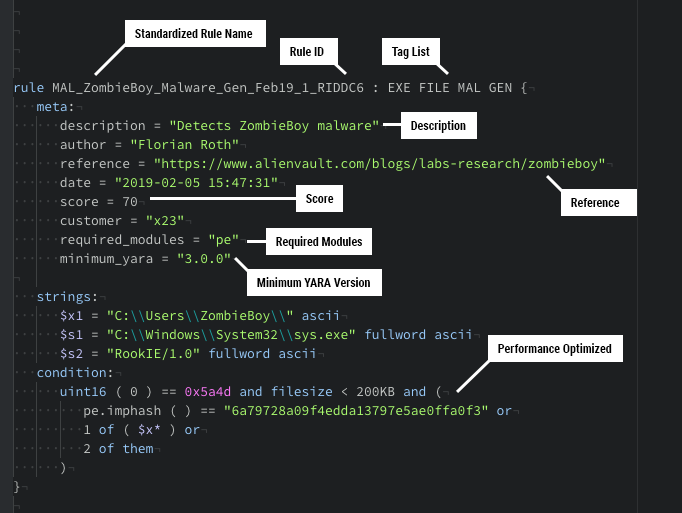
Valhalla Yara Rule Feed Nextron Systems
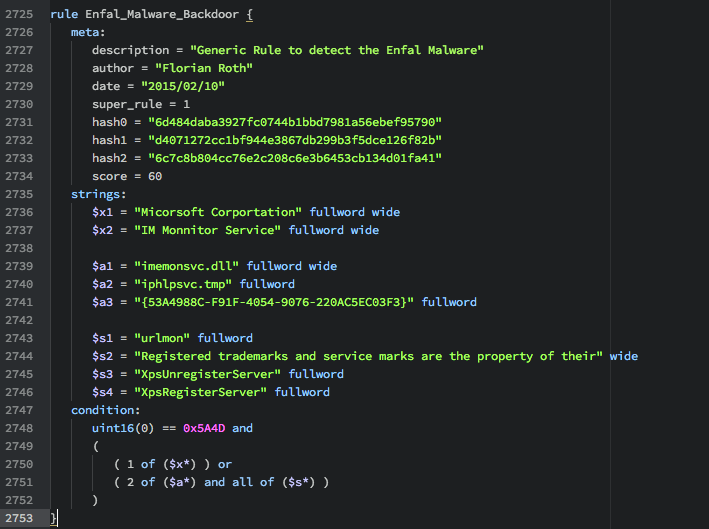
Yara Archives Page 2 Of 2 Nextron Systems

Yara Rule Examples Knowledge Base

Yara Rule Examples Knowledge Base

How To Write Yara Rules Knowledge Base
A Quick Introduction To Yara A Quick And Handy Approach Is We All By Ax1al Ax1al Medium

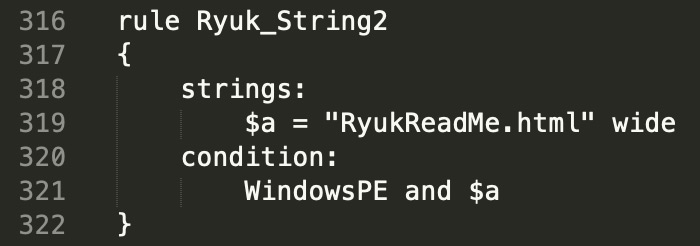

Post a Comment for "Example Of Yara Rule"